Hello its been a long time, since I last posted. So, here I come with a very useful post that is OSSEC, a Host Intrusion Prevention System server & agent installation and configuration. This is not hard to setup, can be done easily in 20 steps.
OSSEC is an open source host-based intrusion detection and prevention system (HIPS) that performs both profile and signature-based analysis to detect and prevent computer intrusions.
OSSEC can perform:
- Log analysis
- Integrity checking
- Windows registry monitoring
- Rootkit detection
- Time based alerting
- Active response.
So we see that OSSEC has evolved quite a bit with these features. Out of all these features, one feature that stands out is the OSSEC's ability to analyses logs. OSSEC has a very powerful logs analyzing engine that is capable of analyzing almost every type of logs that are generated on a system.
File Integrity checking
There is one thing in common to any attack to your networks and computers: they change your systems in some way. The goal of file integrity checking (or FIM – file integrity monitoring) is to detect these changes and alert you when they happen. It can be an attack, or a misuse by an employee or even a typo by an admin, any file, directory or registry change will be alerted to you.
Log Monitoring
Your operating system wants to speak to you, but do you know how to listen? Every operating system, application, and device on your network generate logs (events) to let you know what is happening. OSSEC collects, analyses and correlates these logs to let you know if something wrong is going on (attack, misuse, errors, etc). Do you want to know when an application is installed on your client box? Or when someone changes a rule in your firewall? By monitoring your logs, OSSEC will let you know of that.
Rootkit detection
Criminals (also known as hackers) want to hide their actions, but using rootkit detection you can be notified when they (or trojans, viruses, etc) change your system in this way.
Active response
Take immediate and automatic responses when something happens. Why wait for hours when you can alert your admin and block an attack right way?
There is one thing in common to any attack to your networks and computers: they change your systems in some way. The goal of file integrity checking (or FIM – file integrity monitoring) is to detect these changes and alert you when they happen. It can be an attack, or a misuse by an employee or even a typo by an admin, any file, directory or registry change will be alerted to you.
Log Monitoring
Your operating system wants to speak to you, but do you know how to listen? Every operating system, application, and device on your network generate logs (events) to let you know what is happening. OSSEC collects, analyses and correlates these logs to let you know if something wrong is going on (attack, misuse, errors, etc). Do you want to know when an application is installed on your client box? Or when someone changes a rule in your firewall? By monitoring your logs, OSSEC will let you know of that.
Rootkit detection
Criminals (also known as hackers) want to hide their actions, but using rootkit detection you can be notified when they (or trojans, viruses, etc) change your system in this way.
Active response
Take immediate and automatic responses when something happens. Why wait for hours when you can alert your admin and block an attack right way?
How to Configure OSSEC Server and Agent
Step 2. Run the OSSEC VM from VMware Platform
Step 3. Open OSSEC VM and type “cd /var/ossec” which is the location of the OSSEC. The type “ls” to list out the available files and folder in the ossec folder
Step 4. Open bin folder by “cd bin/” and type “ls” to list out files and folders in OSSEC
Step 5. To run the OSSEC which is a client and server approach, we need to add a client (Agent) in the OSSEC server which is our CENT OS Machine. So, A Agent should be added in the OSSEC server by running the application Magage_agents by using the command “sudo ./manage_agents”
Step 6. Press “A” to add an Agent, then enter the required details like, Name for the agent, IP Address of the agent, ID for the agent
You need to enter the IP Address of the client machine to add it as an agent into the OSSEC server.
To find the IP address of the client machine, go to your client machine and type
For Windows: ipconfig, For Linux: ifconfig
There you can get the IP address of your client machine.
After entering the details press “Y” to add the agent
Step 7. Now a key is to be generated to connect the client to server. So, to generate the key press “E”, then type the ID that you entered while adding the agent to generate the key
Step 8. Copy the key from the OSSEC server
Step 9. Client (agent) should be installed on the client machine.
Client OS can either be a Windows or a Linux machine, Agent application should be downloaded according to respective Operating system.
You can download OSSEC Agent Manager from https://www.ossec.net/downloads.htmland Install it on the client machine
Step 10. Open the OSSEC Application manager and paste the key that we copied earlier.
Step 11. IP address of the OSSEC Server machine is to be added in the OSSEC Agent Manager and click on “Save”
Step 12. After entering the IP address of the OSSEC Server in the OSSED Agent Manger, go to “Manage” à click on “Start OSSEC”
Step 13. Now restart your client machine
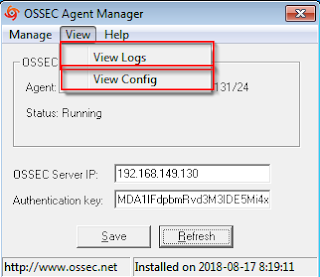
Step 14. Open OSSEC Agent manager à To view the logs or config, click on “View” à “View Logs” or “View Config”.
Step 15. You can view the complete details of agent in the config file
List of programs in the Agent can be viewed as well
Step 16. Now go to the “OSSEC server” and type the following command to check the agent activity and OSSEC Status, first let’s check the status of the OSSEC Server type the command “sudo service ossec-hids status”
Step 17. You need to make sure all the services. If any of the service except maild is not running, we need to start them manually by going into the ossec location
Command is “cd var/ossec/bin”
Suppose ossec-remoted is not running enter the command “./ossec-remoted”
Step 18. Now as the agent is added, we can control our agent easily. To control the agent open agent_control, by using the command “./agent_control”. You can view the list of available options for controlling a agent
Step 19. Type “./agent_control -l” to list the available agents
Step 20. Type “./agent_control -I id” to get the details of the agent
Step 21. The most important activity of the server is to monitor the agents which can be done by checking the logs. Logs of the OSSEC server are stored in “/var/ossec/logs”
Step 22. Go to “/var/ossec/logs” and we can access all the available logs
Step 23. Open “OSSEC.log” which contains all the agents logs
If you face any issues while configuring or installing OSSEC Server or agent, feel free to comment below
========== Hacking Don't Need Agreements ==========
Just Remember One Thing You Don't Need To Seek Anyone's To Hack Anything Or Anyone As Long As It Is Ethical, This Is The Main Principle Of Hacking Dream
Thank You for Reading My Post, I Hope It Will Be Useful For You
I Will Be Very Happy To Help You So For Queries or Any Problem Comment Below Or You Can Mail Me At Bhanu@HackingDream.net